Michael Kaczmarek

Vice President, Product and Marketing
Michael Kaczmarek heads product management and marketing for Verisign’s Security Services product suite. He is responsible for developing the vision, strategies, and tactics for the successful launch and expansion of products into new and existing markets.
Michael has been with Verisign for more than 16 years and has served in various capacities including director of the program management organization, technical operations manager and account manager. Prior to joining Verisign, Michael was a systems engineering manager for Lockheed Martin in charge of their Solid Rocket Motor Disposition in Russia Program. He has also worked as an environmental engineer at Tetra Tech, Inc. and an engineer at SRS Technologies.
Michael is a certified project management professional and certified professional engineer. He holds a Bachelor of Science in aerospace engineering from the University of Maryland, College Park, A. James Clark School of Engineering and a Master of Engineering in environmental engineering from Johns Hopkins University, Whiting School of Engineering.
Recent posts by Michael Kaczmarek:
To establish connectivity with other users and devices, almost anything that interfaces with the internet depends on the accuracy, integrity and availability of the Domain Name System (DNS). Most online transactions and data movement are critically dependent on DNS services.
As such, DNS is an important point of security enforcement and a potential point in the Cyber Kill Chain for many cyber-attacks. Organizations are beginning to recognize this and are using DNS security mechanisms as a first line of defense for preventing or mitigating online threats.
(more…)
Launching a DDoS attack is much more accessible to attackers thanks to the rise of cloud computing, cheap hosting, readily available bandwidth and open-source attack tools. From low-skilled teenagers aiming to cheat while playing online games to cybercriminals looking to supplement their income by renting out their botnets for opportunistic attacks, the DDoS-for-hire market is booming.
(more…)
Layer 7 attacks are some of the most difficult attacks to mitigate because they mimic normal user behavior and are harder to identify. The application layer (per the Open Systems Interconnection model) consists of protocols that focus on process-to-process communication across an IP network and is the only layer that directly interacts with the end user. A sophisticated Layer 7 DDoS attack may target specific areas of a website, making it even more difficult to separate from normal traffic. For example, a Layer 7 DDoS attack might target a website element (e.g., company logo or page graphic) to consume resources every time it is downloaded with the intent to exhaust the server. Additionally, some attackers may use Layer 7 DDoS attacks as diversionary tactics to steal information.
(more…)
This blog was initially published on Oct. 23, 2015. On Nov. 2, 2020, Neustar announced the acquisition of Verisign’s Public DNS. Further information can be found here.
We’ve all seen the check boxes. They’re hidden at the bottom of webpages. You can’t ignore them, but sometimes you forget they are there. They offer to send you deals and coupons. Some even offer to connect you with their partners for similar benefits. Do you check the box?
In these situations you are given a choice of how you want your personal information used. These sites provide the option to trade some of your personal information for a future benefit. If you decide to opt in, your personal information will be transferred, traded or sold to others, and in exchange you will receive something in return, i.e., 10 percent off your next purchase, advance notice of upcoming events, a free gift, etc. If you opt out, you will receive nothing. Regardless of the return, you were given a choice; opt in and receive a benefit for the use of your personal information, or opt out and be content that your personal information won’t be sold.
(more…)
Security professionals agree that a strong security posture is one that is implemented in a layered approach. This layered approach is also referred to as “defense-in-depth.” A defense-in-depth strategy consists of applying security mechanisms across your organization to ensure sufficient coverage against the wide variety of cyber threats.
A comprehensive defense-in-depth strategy requires security mechanisms to be applied through the implementation of hardware, software and security policies. Hardware protection includes, but is not limited to, the implementation of next generation firewalls (NGFW), intrusion prevention systems/intrusion detection systems (IPS/IDS) and secure Web gateways (SWG). Software-based protection is done through anti-virus software deployments, automated patch management or tools for Internet monitoring. Finally, no defense-in-depth strategy would be complete without the implementation of strong security policies that prescribe processes for incident reporting, service and system audits, and security awareness training.
(more…)
There are two types of information that can be found online about you: the information you intentionally post and the information that is automatically collected.
The information that you intentionally post is what you want everyone to know about you. Your professional life is documented on LinkedIn. Your social activities with friends and family are chronicled on Facebook. You alert the world of your immediate thoughts on Twitter. You even choose to provide your address and credit card information when buying things online. All of this personal information about you is deliberately posted and collected with your consent.
(more…)
Today’s new age of ubiquitous connectivity has created an insatiable and growing demand among employees and consumers to be online with familiar systems and tools at all times. Employees are no longer satisfied with the limited choices in devices and tools provided to them by their corporate IT organizations. They want to use what they want,when they want. They believe that choosing their own devices and tools provides them with the highest level of comfort and efficiency. This desire to use personal devices in work environments, referred to as “bring your own device (BYOD),” coupled with the growing cyber-attack surface, poses significant challenges to IT organizations. These challenges are leading such organizations to ask themselves – Are we ready to support BYOD?
(more…)
Defending against cyber threats is not only critical, but increasingly difficult and expensive. Just a quick glance at today’s news headlines and it is clear that these threats present numerous challenges to Internet users and the organizations that both serve and employ them. For example, in 2014, McAfee Labs observed a 75 percent year-over-year increase in new malware equating to 387 new threats per minute. Further, the Ponemon Institute estimates the average data breach costs large organizations $3.8 million per event.
Most solutions either require extensive investment or do not meet an organization’s constantly evolving needs. Traditional, appliance-based security solutions can require organizations to shell out considerable amounts of money, both in up-front capital expenditure and in on-going maintenance fees. Conversely, many managed cloud-based offerings do not provide the critical capability to customize the solution based on an organization’s specific business environment and security needs. Finally, do-it-yourself (DIY) open-source solutions suffer from constant patching and maintenance problems.
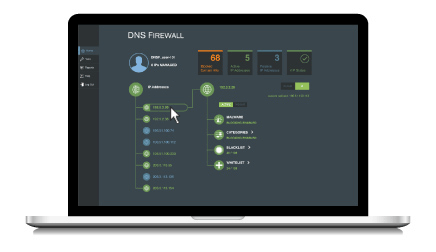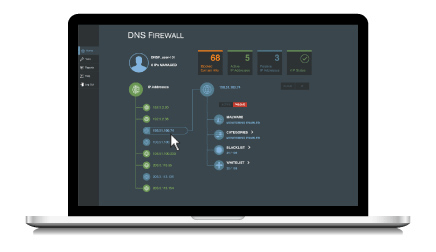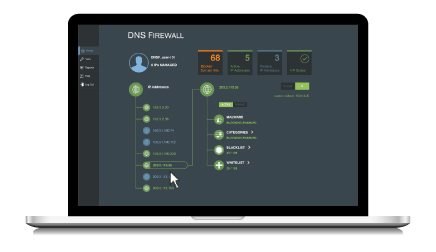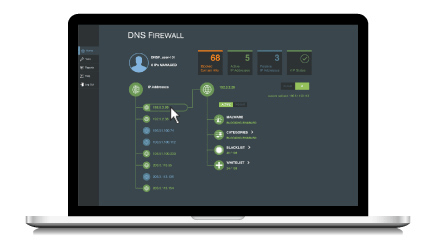
Enter the Verisign DNS Firewall, an easy-to-configure, cost effective managed cloud-based service that offers robust protection from unwanted content, malware and advanced persistent threats (APTs), delivered with the ability to customize filtering to suit an organization’s unique needs.
(more…)
At Verisign, we’ve made the Domain Name System (DNS) our business for more than 17 years. We support the availability of critical Internet infrastructure like .com and .net top-level domains (TLDs) and the A and J Internet Root Servers, and we provide critical Managed DNS services that ensure the availability of externally facing websites to customers around the world.
As we continue to expand our role in Internet security, we are excited to announce the next step in protecting the stability of enterprise DNS ecosystems: Verisign Recursive DNS. This new cloud-based recursive DNS service leverages Verisign’s global, securely managed DNS infrastructure to offer the performance, reliability and security that enterprises demand when securing their internal networks and that communications safely and securely reach their intended destinations.
(more…)